Security for the Ultra Security Conscious
For some years now, the hacker, privacy, and journalism communities have all been debating, discussing, and using the tools I’m about to share with you in this installment. These tools are used not only to lock down your security and anonymity on the known internet, but also to access the portions of the internet that are normally hidden — “The Dark Web.” Despite their usefulness, I haven’t really seen information about these tools shared with the general public in a straightforward, easy-to-understand way. I think it’s worth changing that; while most of us don’t need the same high-privacy, high-security tools that confidential informants, journalists, and whistleblowers use, we should all know about these tools in case the time comes when we actually need them.
Whistleblowing is the act of exposing, for the good of the public, any kind of illegal information or activity. Whistleblowers put their lives and careers in danger to share what they know with the public and have long been an important check on power; this is precisely why there are politicians, organizations, and authoritarian regimes that hate when highly-secure, information-sharing tools are freely available to the public. The freedom to communicate truthfully, securely, and anonymously is a threat to people in power and for that reason you’ll sometimes hear The Powerful suggest that what I’m about to share with you is dangerous.
You’ll hear, for example, that the tools used to surf on the internet anonymously and securely are used by criminals. And that’s true; there are some criminals who use these tools. However, good people — people who fight power with truth, like journalists, whistleblowers, and other ethical informants — use those tools as well. That makes them very powerful and, in today’s increasingly oppressive world, extremely important.
Before I go any further, it’s important to clarify that everything I‘m sharing with you here is currently 100 percent legal, 100 percent open-source, and 100 percent free in the United States. Open-source means there’s a community of software developers who monitor, update, and improve the software; the fact that so many eyes are examining each build (or revision) of the software’s code virtually guarantees that no malicious code can be inserted into the software.
It’s also worth reminding everyone there’s no such thing as perfect digital security on the internet. There are best tools, best practices with those tools, and best setups to take advantage of those tools. But there is no tool — none — guaranteed to protect you online 100 percent, especially if you’re not paying attention.
All any expert can do is to recommend the best tools for the right jobs, and that’s what we’re about to do now. So with that introduction, let’s jump into the deep end of the Deep Web.
TAILS: The Most Secure Operating System in the World (According to Edward Snowden in 2013)

There’s a good reason that the logo for TAILS is a USB plug…
What Is It?!
TAILS is a highly-secure operating system (and a host of cool applications) designed to be booted off of a DVD or USB thumb drive. This not only makes TAILS easy to transport, but also ensures that TAILS can be booted and instantly useful from nearly any PC, Mac, or Chromebook. TAILS is built on Linux, a name you might recognize because it’s a popular, free, and open-source operating system that’s been available since 1991. TAILS, in particular, runs on a variant of Linux known as “Debian,” which became available in 1996. TAILS hit the big-time in 2013, when famed whistleblower and NSA contractor Edward Snowden used the software to contact reporter Glenn Greenwald at The Guardian newspaper in England and documentary filmmaker Laura Poitras. Snowden actually insisted that to communicate all three use TAILS along with all of its various built-in security and anonymity tools.
Why Is It So Powerful?
TAILS is powerful for three reasons. First, it’s as portable as a USB stick, which is far easier and more discreet to carry than a laptop. That portability, along with its software design, makes it easy to run off of nearly any host computer. Second, using TAILS on a host computer in the correct fashion leaves no traceable data behind as to any of its user’s online activities. It even comes pre-packaged with a suite of its own free software tools, allowing its users to work efficiently and without needing to disturb or use the host computer in any way. Third and most importantly, when setup correctly, TAILS helps ensure that all of your communications — email, web browsing, chat, and more — are encrypted, made anonymous, and then routed in such a way that it’s extremely difficult to detect or trace them.
To better explain how this power is provided, let’s start with its name: TAILS. TAILS is an acronym for “The Amnesic Incognito Live System.” As that’s a mouthful — even for a theater major proficient in Gilbert & Sullivan patter songs — let’s break it down, shall we?
The. Well, if I have to explain this word to you, then you have larger concerns than cybersecurity, my friend. #SorryNotSorry.
Amnesic, as in amnesia, because the TAILS system is designed, by default, to forget everything. It does this by not using the computer’s hard drive to store information. It uses the computer’s RAM (or memory sticks) instead. Because RAM is erased when a computer is shut down, TAILS leaves no trace once the computer hosting it is shut off. By default, each and every time you power TAILS back on, you are presented with the equivalent of a brand new, freshly imaged computer that’s never been used.
Incognito, as in “undercover,” because TAILS is designed to work anonymously and, therefore, protect your identity. It does this by forcing all outgoing connections through the TOR network, a technology I reviewed earlier on in “The Firewall.” TOR (an acronym for “The Onion Router”) is a system of relays which makes tracking anyone’s online web browsing extremely difficult. The TAILS operating system takes using TOR to an extreme: it forces all key communications over TOR, including web browsing, email, internet chat, and more.
Live, as in “living,” because, in the tech world, a live system is a system that is only installed onto a CD, DVD, or USB thumb drive. Nowhere else.
System, as in “operating system” (or OS), because TAILS is an entire operating system, just like its cousins Windows, Android, mac OS, and iOS. Unlike its cousins, however, TAILS is designed to be small, portable, and extremely secure.
How Do You Set It Up?
While I’m a huge fan of having TAILS out there as a tool for those who need it, its setup process is convoluted and takes hours. I mean that literally: two hours. Just have a look at the Mac installation page or the Windows installation page if you think I’m kidding:
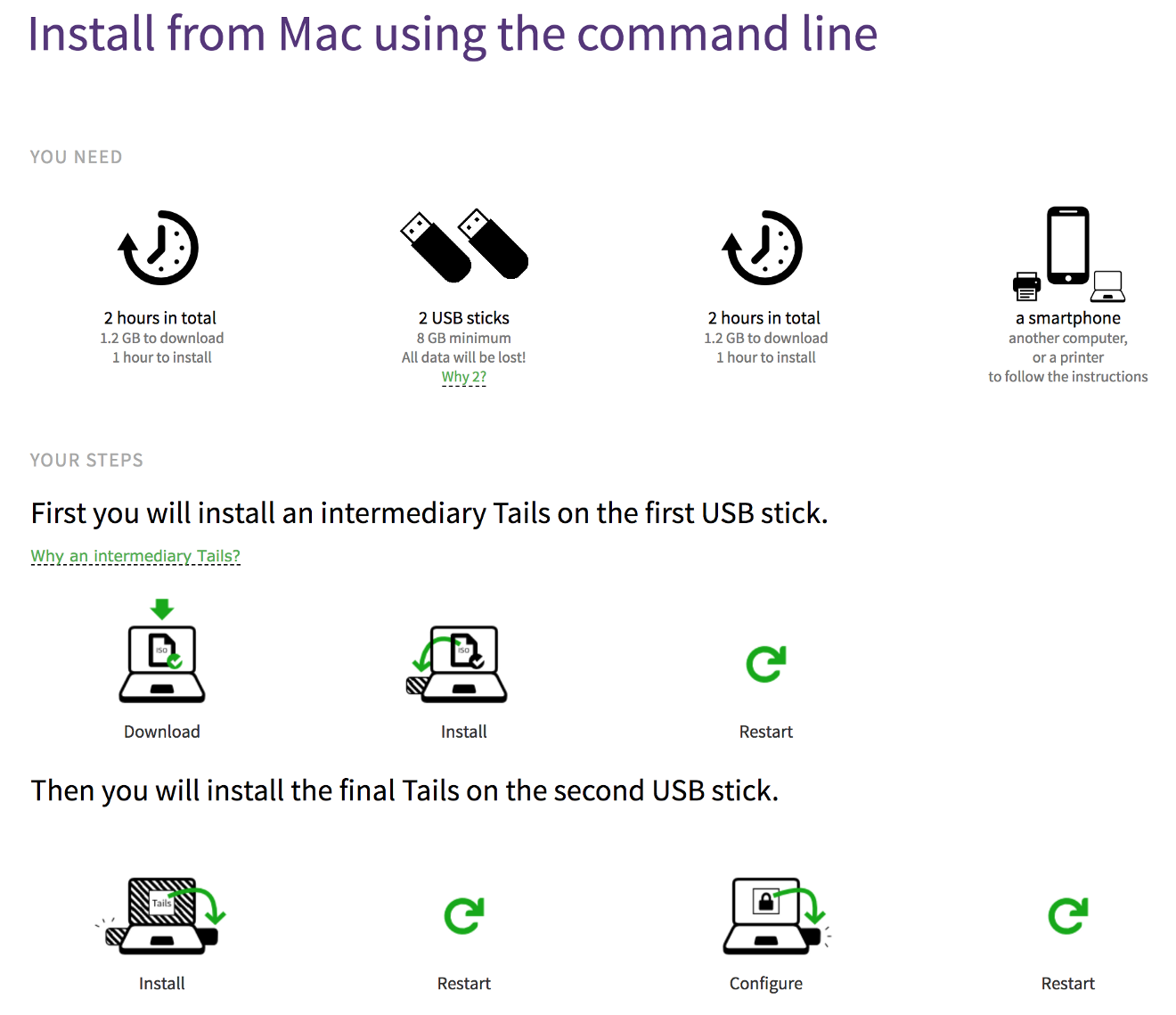
That’s right, friends — the setup on a Mac or PC requires 120 minutes, seven steps, three restarts, two USB sticks and — most likely — one massive headache. As a bonus, if you’re not fully frustrated or scared yet, the setup on a Mac also requires you to type out a UNIX command that looks something like this:
sudo dd if=tails-amd64–3.8.iso of=/dev/disk3s1 bs=16m && syncIf you don’t know what that means — and most of you don’t — TAILS provides a primer on how to add that command; but still, don’t expect tech pundits like Leo Laporte, Walt Mossberg, David Pogue, Jean-Louis Gassée, and The Kim Komando Show to tell you how fun and easy TAILS is to set up. It just ain’t.
What Kinds of Tech Does it Provide?
TAILS provides a host of great, free, open-source applications and tools to help ensure that (a) there’s an app available for everything you need to do and (b) all that you do online is secure and anonymous. If you’re wondering just how powerful these tools really are, many of them are known by the NSA to be difficult or impossible to break. This includes:
- The TOR browser, for safe internet browsing
- KeePassX, a great application for generating and safekeeping of all of your various passwords
- Thunderbird, for emailing, secured by the Enigmail extension to encrypt and authenticate emails using a well-know and secure protocol called “OpenPGP”
- Pidgin Instant Messenger, for live chats, which are secured by the Off The Record (or OTR) encryption
- OnionShare, for safe sharing of files over the TOR network
- LibreOffice, for open-source versions of every standard office application you’ve come to know and love
What’s It Look Like?
When you boot into TAILS, it looks and works in ways that should be recognizable, whether you’re used to a Mac, Windows, or Linux operating system: you double click to open folders, you single click to open a menubar, you have a home folder where you can keep files, and there are system options that you can alter to suit your preferences. Here’s a video I made to give you a simple and quick look at what the desktop looks like when you boot into TAILS. I should mention that I made this video by booting TAILS into a virtual machine (or VM) and then recording my screen. Please note: never use TAILS in a single VM if you need to ensure your anonymity and security.
What Are The Caveats?
- It’s not for everyone. TAILS is not the kind of OS that people like you and I use for everyday computing. Instead, it’s designed for specific people whose specific communications need to be as secure and anonymous as possible. Journalists, whistleblowers, and people living in repressive regimes where freedom of speech is restricted or punished would benefit from using TAILS.
- It’s not 100 percent foolproof. TAILS is updated on a regular schedule precisely because flaws are found and fixed in their code. This happened, notably, back in 2014. TAILS even published a page of possible ways that its own security can be compromised. Some of the methods they describe involve hacking methods but others involve a lack of personal responsibility on the part of those using TAILS. That means you: if your online behavior isn’t as secure as your digital tools, TAILS won’t protect you. For more advanced users, it’s worth knowing that TAILS knows key information about the computer to which it’s connected: the IP address, the name of the WiFi network it is connected to, and the serial number of it’s hard drive. Those are key points of entry for advanced malware.
- It ain’t easy to setup or update. I mentioned this earlier but it’s worth mentioning here again. It’s super hard to set up, unless you’re using a computer that’s already running some kind of Linux OS. Even then, most Macs won’t be able to use the built in WiFi card, although wired connections and some usb wireless adapters work.
- U.S. spy agencies hate it. The NSA, in particular, seems to really dislike TAILS. It and the other U.S. spy agencies are, most likely, already monitoring anyone who even visits the TAILS website, let alone downloads and uses the still 100 percent legal and 100 percent free software. As recently as 2014, the NSA even branded TAILS as “a mechanism advocated by extremists on extremist forums,” so they’re not fucking around here. This is ironic, given that TAILS gets 35 percent of its budget from entities related to the U.S. Government.
My thoughts on the matter are two-fold. First, if whistleblower-provided documents now reveal that our spy agencies hate TAILS that much, then I assume it must be a tool that does it’s job extremely well. That gives it value, especially because the NSA didn’t willingly release this documentation. Second, our desire to be assured of our privacy — both online and off — doesn’t make us extremists; it makes us citizens of a Democracy that values, dignifies, and emphasizes the right to privacy.
I get it. If I were a spy, I’d be frustrated by tools like TAILS as well. How are the good men and women who are charged with keeping U.S. citizens safe supposed to stop acts of unthinkable depravity if anyone can communicate privately and anonymously using tools like TAILS? It’s a worthy question, but I’m convinced that the answer to that question isn’t taking away the legal digital tools or the Constitutional rights of law-abiding citizens; rather, it’s finding or inventing new and better ways to focus on criminal intent and behavior.
A hammer can be used to build a house or to bash someone’s head in, but the tool shouldn’t be made illegal.The Bottom Line: Difficult Setup That’s Worth the Effort
Be a renegade and check out the TAILS website. It’s an excellent, strong, and very portable way for those in need to have extreme security and anonymity online. It can run discreetly on nearly any computer that’s available because it leaves no trace behind. It’s intended for those who must protect their careers (and, possibly, their lives) which is why the difficult and lengthy setup is worth the (free) price of admission.
WHONIX: A Virtualized Operating System Designed for Advanced Security & Privacy

Whonix (pronounced “HOOnix”) is an OS focused on anonymity, privacy, and security. Like TAILS, it is built on the open source Debian Linux OS and on TOR, the decentralized network which randomizes and segments your data transmissions. Its unique approach to offering such well-regarded security is the creative use of two virtual machines (or VMs) running in tandem on one host computer. One of these VMs is known as the Gateway while the other is known as the Workstation. The Gateway is VM that’s responsible for running TOR and for channeling all information from the Workstation over the internet via that TOR connection. The Workstation VM runs all user applications and sends all outgoing data onto the internet via a special and isolated connection to the Gateway VM. If you’re confused by that, then this image, from the Whonix website, will surely help explain how the systems are made to function with one another:
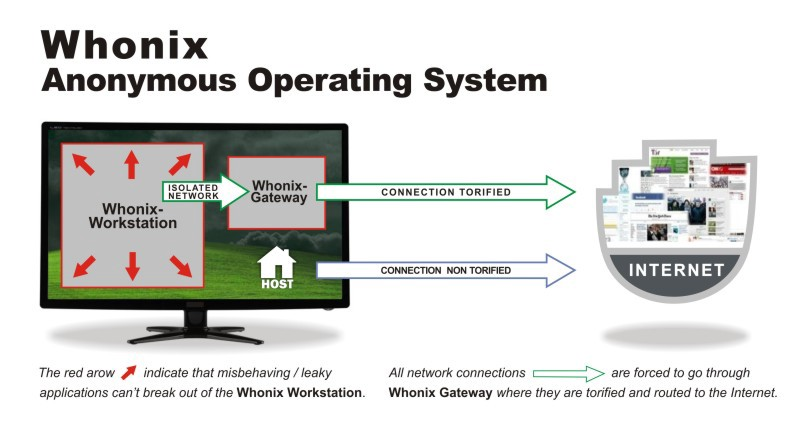
How Whonix works, as seen on their homepage.
Why Is it So Powerful?
Whonix provides a number of powerful benefits. First, the unique double-VM setup of Whonix offers advanced protections from malware, digital snooping, and from both network and data leaks. A malware attack on one VM, for example, won’t spread to the other VM or to the host OS. Second, if you’re taking advantage of VM snapshots (and you should!), then any damage to a Whonix VM can be quickly and easily rolled back to its last pristine state. Third, the two IP addresses used in each of the two Whonix VMs are different than your physical computer’s actual IP address, protecting you from digital snooping when using Whonix for your browsing, emailing, and other online activities. Lastly, because Whonix is made to use within a VM and still provide apt security, it’s far easier to use than tails.
How Do You Set it Up?
Compared to TAILS, setting up and updating Whonix is a breeze. Even if you’re on a Mac, there are only four steps and those take about an hour to complete. Step one is downloading the two Whonix VMs which takes the bulk of that hour. Step two is downloading and installing the 100 percent free and open-source VirtualBox application made by longtime stalwart Oracle. Step three is importing each of the two Whonix VMs into VirtualBox the correct way. Step four is launching both VMs to get started! Updating Whonix is equally easy and can be run from inside of each VM.
What Kinds of Tech Does it Provide?
Compared to TAILS, Whonix only provides a few free, open-source applications and those need to be set up fairly extensively. The list includes:
- The TOR browser, for safe web browsing
- Firefox, for less secure web browsing
- Icedove, for emailing, secured by the Enigmail extension to encrypt and authenticate emails using a well-know and secure protocol called “OpenPGP”
- HexChat, for internet chats
- VLC, to open and view every kind of video file that’s ever existed
What Does it Look Like?
Not surprisingly, the Debian OS of Whonix looks and behaves similarly to the Debian OS in TAILS. Moving around the desktop and opening folders and menu-bar items is straightforward. Unlike a Mac, the main menu bar is at the bottom right, not the top right. Here’s a short video I made to help demonstrate launching each of the two Whonix VMs from VirtualBox to start using this unique system.
What Are The Caveats?
- It requires a specific and modern computer. While TAILS can boot from most any computer, Whonix requires that you travel with a specific computer (most likely your own) that’s been setup in advance with VirtualBox and the two Whonix VMs. Additionally, it’s best to install Whonix on a computer that has a minimum of 8GB of RAM, although 16GB of RAM is far better. Whonix can function with less RAM, but it loses its graphical user interface (or GUI). I’d suggest avoiding this as both beginner and intermediate users will find a text-only OS very difficult to manage.
- It‘s not amnesic. When you shut down TAILS, it wipes itself clean and leaves no trace behind. Not so with Whonix. If you download files or keep emails on the Workstation VM, those files will remain available when you reboot the Workstation VM. That doesn’t make Whonix less safe, it just means you need to be more careful.
- Shared folders with the host OS are verboten. If you decide to use Whonix, you should never, ever, ever set up shared folders between the Workstation VM and your host operating system. Never. Doing so introduces a way for malware to penetrate from the Whonix VM enclosure and onto your own computer — a huge no-no.
- Additional customization is required. If you need or would like like any additional, free, open-source software like LibreOffice, Thunderbird, or KeePassX, then you’ll need to download and install each of those items, one at a time, into the Whonix workstation VM. TAILS, by comparison, comes pre-packaged with all of these software titles built in — a nice convenience.
- It’s not for everyone. Kudos to the Whonix team for making both the setup and the updating of Whonix extremely easy. Despite that ease, the product is still designed for those individuals who are willing to tinker with virtual machines and have some experience in downloading and setting up new operating systems. There’s no help line to call, although Whonix does provide a very complete set of documentation along with a Whonix message board where other users and super users can help answer some of your questions.
The Bottom Line: Easy to Setup, Great Security, & Geared For Intermediate Users
Whonix is another great tool in the security arsenal. With a very easy setup, it provides security and anonymity that aren’t possible with regular computing. Because Whonix provides every VM you’ll need to use their software, there are only a few steps required to get started with this clever concept. However, Whonix requires more customization, so users will be tasked with making those customizations on their own. Many will therefore need to get familiar with the free Debian OS on which Whonix is based. Most importantly, Whonix isn’t amnesic, something that the most secure users will need to consider before using this as a solution.
Is it the right solution for you? Whonix provides a handy chart comparing its technology to TAILS and other secure solutions. It’s worth noting that the security community actively debates which OS — TAILS or Whonix — is the best solution. ...
Honorable Mentions: Qubes, Kali, & Combinations
“Honorable mention” might not be the best phrase to describe these choices, given the strong passions that people have for each of these tools and approaches. As strong passions are fueled by strong approaches, let’s take a quick look at each of these solutions — they’re all creative approaches for the challenge of wanting best security.
Qubes: The Most Secure Operating System in the World (According to Edward Snowden in 2016)
 This is, easily, the funniest tag line in all of technology…
This is, easily, the funniest tag line in all of technology…
If I’m going to make recommendations based on Edward Snowden, then I should be more current. In 2016, Snowden threw his support behind a relatively new OS called Qubes, an approach to computing that’s very much like having virtual machines on steroids. For starters, it’s fast: unlike booting into the macOS or Windows and then running a virtual machine application like VirtualBox, Qubes is the OS. That means all of your qubes are running natively on your computer (something us dweebs call a “bare metal hypervisor”), a huge advantage for speed and security.
Once booted, Qubes offers unlimited VMs, or, as the company calls them, “qubes.” Each qube is segmented into its own network, so it can run independently of every other qube. This segmentation is important because if one qube is infected with malware, the others qubes remain unaffected; this means that any digital intrusion can’t jump from qube to qube and destroy your entire setup — a huge benefit. The default installation of Qubes pre-configures your system to have three qubes: work, personal, and untrusted, but you can create as many qubes as suits you. You can even create what the company calls a “single-use disposable qube” which can be used, for example, for downloading an unknown or potentially dangerous attachment, isolating it from the rest of your computer and from other qubes. The OS is designed for multiple qubes to run simultaneously and each qube is conveniently color-coded, so users can easily tell the difference between them. Here’s a demo I did not make that shows you the Qubes OS in action:
I didn’t make this video because I couldn’t set up Qubes on my Mac!
While Qubes is beloved by the security community, there are a few caveats to know before using the software. First, you’ll need specific hardware to install the software. Qubes keeps an extensive list of what works and if you’ve got an Asus, Lenovo, Dell, or HP computer then you’re probably in luck. If you’re on a Mac, your options are few and far between. Second, the installation process is convoluted and requires using the command line. If you like an extreme challenge (followed, hopefully, by an extreme cocktail) getting the OS working on a Mac is, shall we say, nutzo.
Kali: The Operating System for Testing Security
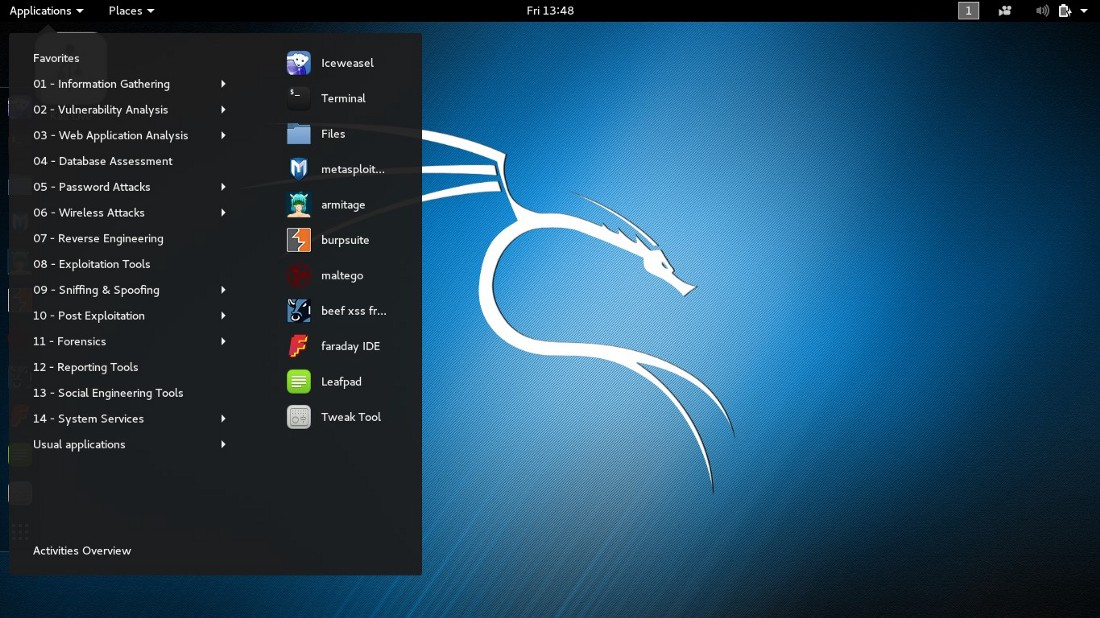
Kali was developed in 2013 for very specific purposes: digital forensics, reverse engineering, and penetration testing. Now don’t get your knickers in a bunch, kids — penetration testing or “pen testing” is when security experts run tests to prove how secure an application, an operating system, or a network truly is. The company behind Kali, “Offensive Security,” offers training on their software (Kali is but one title in their library) and a certification if you complete their course. But a funny thing happened on the way to the digital forum: a community of users sprang up around the OS and began using it as a secure environment in the way that TAILS, Whonix, and Qubes are used. Like TAILS and Whonix, Kali is based on Debian linux and comes with tools to help keep you anonymous online. Like TAILS it’s best when running off of a USB stick and is fully amnesic, so it won’t leave behind any traces of what you do on a host computer.
That being said, Kali isn’t as fully-functional as TAILS or Whonix, so it’s best left to advanced users, the extremely curious, and security professionals. In that regard, Kali is pre-loaded with about 300 software tools geared for testing everything under the sun. Just take a look at the picture above — there are no less than 14 different categories of applications that Kali provides to help you test your own computer or network. In fact, Kali is quite popular with the kids for trying to crack (or break) a WiFi password. Here’s a quick look at Kali:
Combining Security Solutions For More Fun
Some folks who are extremely serious about their security combine approaches. If running Whonix or Kali isn’t enough security for you, for example, you can actually run both of those OS’s inside of Qubes. Wait, what?! That’s right! Qubes allows you run Whonix inside of its environment. Whonix has a page devoted to this approach as well. The setup looks to take about 15–30 minutes and offers compounded security with both virtualization and segmentation.
Qubes also offers the ability to run Kali inside of its segmented walls, if you’d like to give that a try.
If you’ve got a special approach to security on your setup, please share details in the comments below so we can all learn more. The more people using safe and and secure approaches, the better — especially regarding the TOR network, which only gets safer as more users join.
Wishing you all well until we meet again and, until then…surf safe!